Tips and Pointers to Avoid Data Leaks

Reading in the newspapers about patients, students, employees, etc. personal data literally lying in the streets is something that is almost a daily occurrence. Perhaps a USB was lost, files were put out as waste paper, or a smartphone was stolen.
When a third party who should not have access to certain data holds personal data, this means that there is a data leak. The risk of data leaks is becoming higher and higher, being as personal data is now stored on such a vast array of databases.
Adverse effects on the privacy of the individual involved can be caused by data leaks due to the fact that the data leaked can be misused. One example of misuse is identity fraud, other possibilities are also infringement of anonymity and undesired profiling.
Due to various incidents in which quite ample amounts of personal data became exposed, there arose a need for ways of better protecting and securing data. In the Netherlands that result has been the introduction of a Dutch law, included in this is an obligation for the parties who are responsible to report any data leaked that were caused due to a security error.
This security error could be due to organizational or technical failure, such as the loss of a USB stick, an email which was sent to the wrong sender, poor password management, or human acting that is deliberate such as hacking.
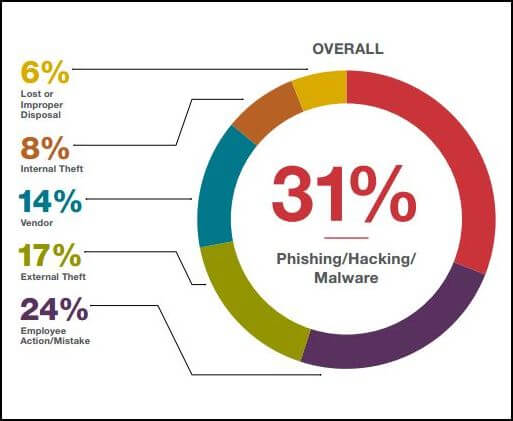
The notification obligation should, according to the Dutch legislator, bring about more awareness, this will hale achieve better preserving, and as a result restore the confidence in the handling of personal data.
With a notification obligation being introduced, the responsible party is not under obligation to report the leak. This will cause educational and research instructions which process personal data to be forced to report certain breaches in security which result misuse, loss, or theft of personal data to the Dutch Data Protection Authority as well as to the person concerned. This is how data leaks which have an impact which is unnecessarily large on the privacy of the individuals which are affected will be prevented. If you want to know the impact of data leaks, then read this piece from Barclay Simpson.
So, how will company be aware of when a data leak should be reported? Basically, the three questions below must be answered affirmative:
- HAs there been a security breach, in other words a data leak?
- HAs the processed data been lost or exposed to processing that is unlawful because of this breach?
- HAs said exposure caused any serious or likely adverse effects of protecting the privacy or those involved or that of the processed personal data.
If the requirement of notification is not met by an institution, they risk a large fine of up to 810,000 euros, or even 10% of their yearly revenue. In practice, there are not many companies that are sufficiently aware of what their obligations are under privacy laws, and this maybe the same case when it comes to their obligation of reporting data leaks. Hopefully a fine like this will guarantee that institutions abide to the guidelines in regards to data breaches.
How are institutions and companies able to prepare for this law on the subject of notification obligation? Here are a few guidelines:
- Chart the organization´s data streams.
- Check security measures which are currently in place.
- Where necessary, asses any potential risks of data being lost and adjust security policies where needed.
- Create an internal procedure, in other words an action plan that is clear.
- In regards to processing of personal data, maintain a strict policy.
- Have an inventory made of any contract with the processors and where necessary, adapt.
- Take encryption into consideration so that notification can be omitted.
Will the end result be a data world that is safer? It is certainly our hope, it still however remains to be seen. This is a subject we will most definitely keep you up to date on.

Comments